Table of Contents
A Distributed Denial of Service (DDoS) attack is more powerful in terms of its impact, the effort required in curbing the damage, and the flood of traffic it carries to the target. Detection of threats relies on tools and knowledge about common signs and occurrences around an attack. The question, ‘How to know if you got DDoSed,’ fetches answers that talk about sophisticated tools that monitor attack vectors, and leverage automation to block attacks.
A Sophos report explained DDoS attacks thus – “Here, a network of hacked computers (bots), also called “zombie computers,” are used to form a network of bots or a botnet, which is then leveraged to send huge quantities of illegitimate data to servers, websites, and networks to bring them down.”
History of DoS and DDoS attacks
Cyber attacks have been undergoing transformation to defeat detection tools that prevent them from causing damage to the system and data. Tracing the history of DDoS attacks, it was first detected in 1974 and was launched by a 13-year-old ‘computer geek.’
“The first-ever DoS attack occurred in 1974 courtesy of David Dennis—a 13-year-old student at University High School, located across the street from the Computer-Based Education Research Laboratory (CERL) at the University of Illinois Urbana-Champaign,” a Radware report read.
David compiled and sent an ‘ext’ command to several terminals all at once just to see what happens next. It led to all the targeted 31 users losing connection to the power. This attack was curbed by turning off the default setting of accepting ext commands.
Today, DDoS attacks are a method used by hackers including NoName, and Anonymous Sudan that render the portal inaccessible for hours to days.
How to know if you got DDoSed
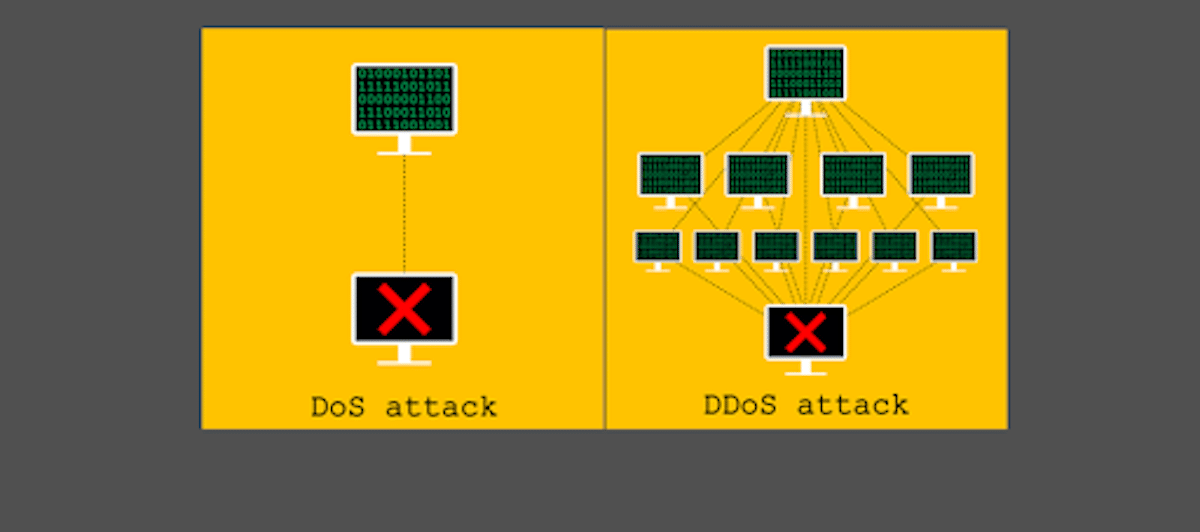
While a Denial of Service attack (DoS) sends an unexpected and very high volume of traffic to a targeted device using one system which may cause it to shut down, a DDoS attack uses several systems to target a device. Knowing if you got DDoSed needs tools and knowledge of changes witnessed in such attacks offered in cybersecurity news and threat intelligence reports.
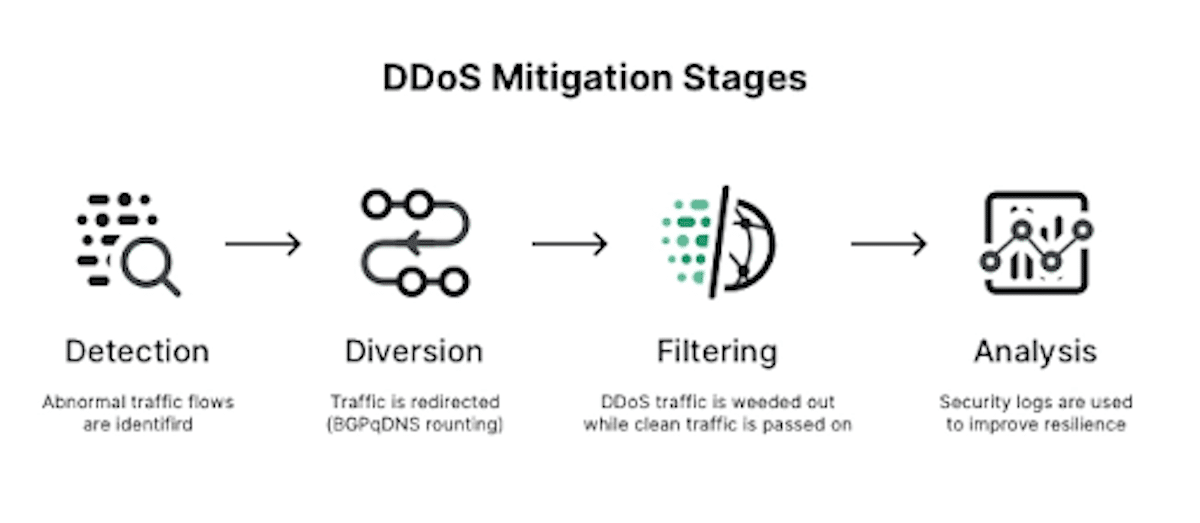
This report will detail how to know if you got DDoSed and the tools and methods used to detect sudden and massive incoming traffic. Traffic flow deviations help in the early stages to see how a buildup of DDoS assault is incoming and lead to better prevention of attacks before it hits the network.
Tools to identify changes in the pattern that distinguishes legitimate and suspicious amounts of traffic can help in diverting the traffic away from the systems via Domain Name System or Border Gateway Protocol.
System logs and analysis reports can offer data about attacks which helps in identifying hackers and further gives handy data about attack details.
Key features in tools that detect DDoS attacks
Several tools and software offer both threat intelligence and strategies to analyze threats via a cloud-based dashboard. While DDoS protection tools need real-time monitoring and automated checking of the traffic, alerts on incoming and a massive flood of requests must be sent at least seconds in advance.
Artificial Intelligence to know if you got DDoSed
There are several methods to know if you got DDoSed using tools created by artificial intelligence. Naming the most popular methods of DDoS detection, an MDPI report read, “Decision Tree (DT), K-Nearest Neighbor (KNN), Artificial Neural Network (ANN), Support Vector Machine (SVM), K-Means Clustering, Fast Learning Networks, Ensemble Methods, and others are the most popular ML methods used for DDoS detection in SDN (sometimes called Shallow Learning).”
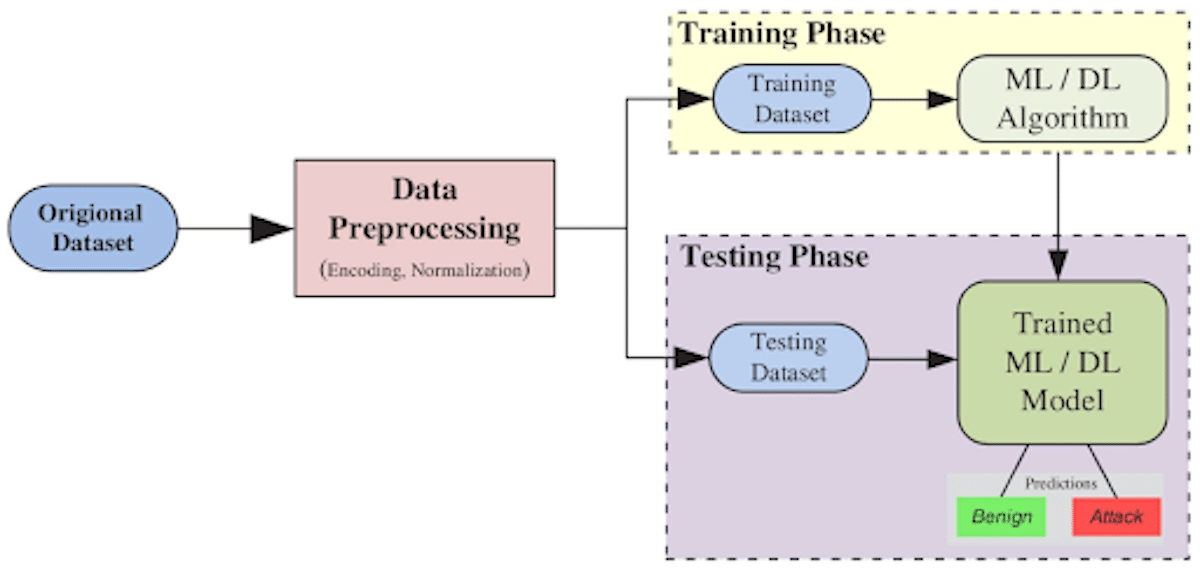
Here is a small introduction to some of the above named machine learning methods that come in handy in early detection to know if you got DDoSed –
- Decision Tree – This method uses a set of rules to classify data and predict possible outcomes. In this algorithm, the DT selects the most optimal attributes based on the best performance to curate a mechanism to detect a DDoS attack.
- K-Nearest Neighbor – This method uses the concept of ‘feature similarity’ to classify data samples by comparing the information. This helps researchers understand the class of data samples. This is also used to reduce the dataset imbalances in detecting a DDoS attack and gauging the performance of the K-nearest neighbor method.
- Artificial Neural Network – Inspired by the human nervous system, this method uses neurons that work as processing units with an input layer, and an output layer besides other features. This method helps in nonlinear modeling by understanding larger datasets.
Helpfulness of tools used in handling DDoS attacks
Although there are several software, vendors, methods, and approaches to know if you got DDoSed or to detect and prevent a DDoS attack, no technology is fool-proof, as research points out. While detection is paramount to the safety of an enterprise, it comes with its own shortcomings. Some of them include sifting through relatively larger datasets, discrepancies in datasets from actual attacks and test attacks, and confused ML models that cannot differentiate between similar datasets.
Companies need to disclose DDoS attacks to researchers for a complete analysis to be able to defend against similar attacks and help them to create more realistic DDoS detection software. To know if you got DDoSed, prevention using both automated tools and machine learning models needs to be used.
Feature Image Credit: (Sophos Home)